FEATURE DESCRIPTION

1. State-of-the-art, Comprehensive, Customized and Indigenous NextGen SIEM Solution.
DetAct – the indigenously developed NextGen SIEM solution – helps in accomplishing the fundamental missions of SOC — continuously monitor and improve an organization’s security posture while preventing, detecting, analyzing, and responding to cyber security incidents with the aid of both technology and well-defined processes and procedures — at a low total cost of ownership.
2. Security Operations Platform for NextGen Threat Detection and Response.
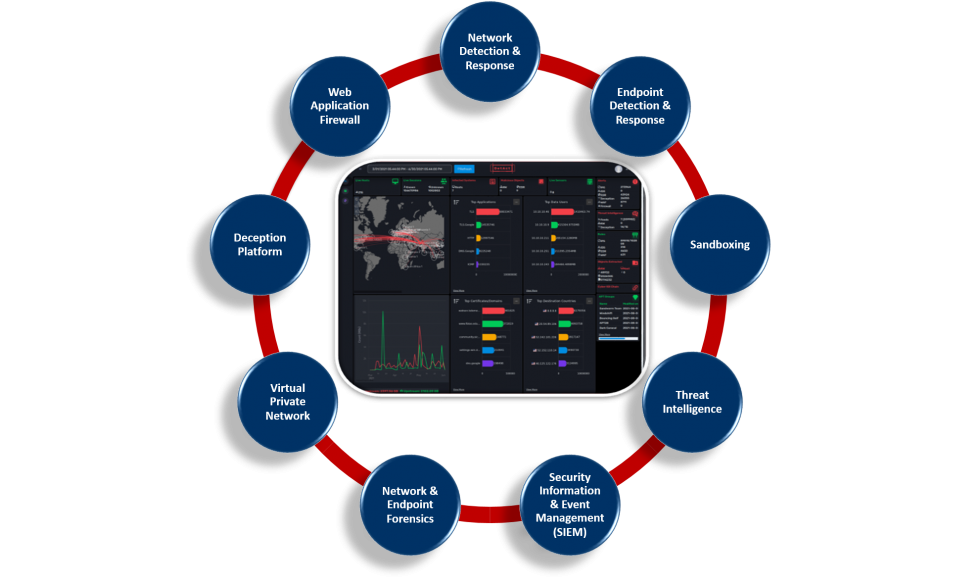
A complete security operations platform with next generation threat detection and response capabilities both at network (network detection & response) and endpoint (endpoint detection & response) level providing a holistic view of enterprise security. DetAct execute and analyze malware/ threats in a secure environment to strengthen threat intelligence and along with network data capture, centralized threat hunting, forensic and visualization.
3. Ingests real-time enterprise-wide vast amounts of security information and event data
DetAct ingests real-time enterprise-wide vast amount and a variety of data types from a wide range of sources, including the following: — Endpoint data: from the Windows event log, Sysmon, EDR solutions and more — Network activity data: from network traffic e.g., applications, process IDs, bytes sent, bytes received, local address and port, remote address and port, and more. — Vulnerability data: From intrusion detection systems, intrusion prevention systems, deception platforms, threat intelligence platforms and more.
4. Gains complete visibility into security data from a single pane with investigation capabilities and real-time alerting
DetAct gains complete visibility into security data from a single pane with investigation capabilities. It eliminates the blind spots across the entire enterprise — from enterprise endpoints to the enterprise–network. It allows searching across various logs and other machine data to find the answers organization need and know what’s happening across the enterprise environment. One can quickly search across the enterprise’s vast amount of data to answer any question, identify IT and security events augmented by real-time alert, and troubleshoot operational issues.
5. Applies advanced analytics and hybrid analysis to accurately detect known and unknown threats
As attackers become more sophisticated in their techniques, known threat detection is no longer sufficient on its own. Instead, organizations must also have the ability to detect slight changes in network, user or system behavior that may indicate unknown threats, such as malicious insiders, compromised credentials or fileless malware. DetAct accurately detects known and unknown threats by analyzing network, endpoint, asset, vulnerability and threat data using state-of-the-art anomaly detection algorithms and hybrid analysis.
6. Reduces events into a prioritized list of the most important alerts
Security teams are burdened with a high volume of alerts, manual tasks, and limited staff, often leading to burnout and weakening of the organization’s security posture. DetAct aggregates related security events and prioritizes them based on various criteria e.g., severity of the threat, criticality of the assets involved, inbound/outbound traffic behavior, etc. Security analysts can then easily see risky users, view their anomalous activities, and drill down into the underlying log and flow data that contributed to the security alert.
7. Automatically parses and normalizes logs
DetAct provides security team with a centralized visibility into disparate security data by first automatically parsing and normalizing both logs and flow data, generated across the enterprise network, and then storing in a database.
8. Provides actionable insight into the most critical threats
DetAct provides actionable insight into the most critical threats by gaining understanding of which systems communicated with each other, which applications were involved and what information was exchanged in the packets. By correlating this information with other network, log and user activity, security analysts can uncover abnormal network activity that may be indicative of compromised hosts, compromised users, or data exfiltration attempts.
9. Supports integration of third-party Threat Intelligence feeds via STIX/TAXII/Reports & other standard formats
DetAct supports integration of third-party threat intelligence feeds in the form of Structured Threat Information eXpression (STIX) mainly via Trusted Automated eXchange of Intelligence Information (TAXII).
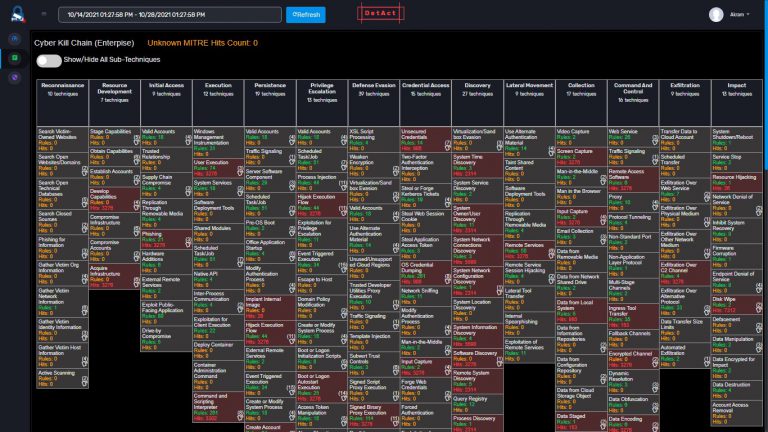
10. Maps threats to Industry-standard MITRE ATT&CK for improved root cause analysis
DetAct maps the investigation of a cyber attack to the MITRE ATT&CK framework, so security teams can visualize attacker tactics and techniques, drill into events and flows by ATT&CK stage and make more confident decisions.
11. Drives compliance and manage regulatory risk
DetAct provides the transparency, accountability, and measurability critical to an organization’s success in meeting regulatory mandates and reporting on compliance. The solution can support compliance to organization compliance policies (monitoring of external hard drives, USBs, Plug & play devices etc) and international regulations e.g., General Data Protection Regulation (GDPR), Sarbanes-Oxley (SOX), HIPAA, ISO 27001, Payment Card Industry Data Security Standard (PCI DSS).
12. State of the art Cyber Threat Intelligence Platform to manage and capitalize cyber threat knowledge
DetAct provides a dedicated and standalone Cyber Threat Intelligence Platform that allows organizations to prevent (via predictive intelligence) or mitigate cyber-attacks by covering/ providing all levels of Cyber Threat Intelligence (Strategic, Operational, Tactical). The platform provides context and understanding/ identifying their adversaries — like who is attacking your organization, what their motivation and capabilities are, and what indicators of compromise in your organization systems to look for — that helps your organization make informed decisions about cyber security.